Hey folks, I just wrapped up some good training on the new “big bad” virus that’s been all the rage lately. I thought I’d take a few minutes of your time to give everyone some helpful information on how to avoid it, and answer some basic questions regarding the virus should anyone get asked by our clients (or potential clients!).
For those who haven’t heard of this virus, it’s called Cryptolocker and on the list of friendly things…….it’s not on that list.
All I’m saying is that the creators of the virus TOTALLY received coal for Christmas.
What the virus does:
It will encrypt files on your computer, and demand a ransom to unlock the files. The files that have been encrypted with a AES256 key, which is the same tech the NSA uses for their files.
Which means that it’s not breakable.
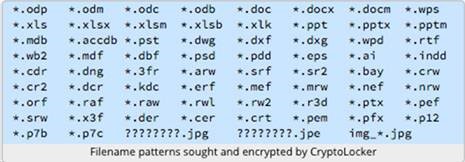
Once on your computer it seeks files of the following types:
If you attempt to access any of your files it will prompt you with a screen much like this one:
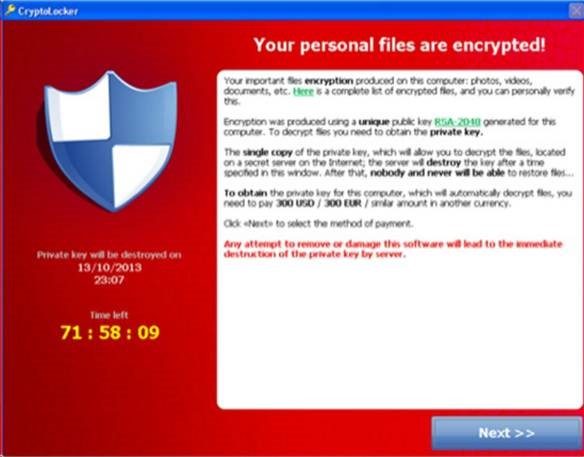
Giving you a few days to pay the ransom to release your files.
This is a serious, very real virus that has already hit the clients of one of our Partners. As of right now, neither the FBI nor any major AV Manufacturer knows of anyway to “un-do” the encryption once it has taken place. Your only options are to pay (which the FBI does NOT recommend) resort to a back-up, or not get your files ever again.
As you can see the list of file types is long and extensive. Every thing from pictures of your first date to CAD drawings of the latest engineering marvel. Excel documents and the latest crime novel. Pretty much if its something special, it will find it, and lock it.
HOW TO AVOID/PREVENT IT:
“Well that’s scary stuff Master J” is what you’re saying. I know….its very very serious and not something to be toyed with. Again, some of our partners have already come in contact with this. I believe the client paid the ransom to unlock the files.
So what do we do?
Well, the biggest and best solution is TO HAVE CONSTANT, UP TO DATE BACKUPS. This is very important for our clients, and us as individuals. IF there is a good back up, and all of the other precautions fail, getting the files locked is no problem. All you have to do is restore the back up and go on your way. Good guys -1/ bad guys – 0.
The virus is usually found in the age old practice of Spam. Most of them spam messages contain some type of attachment like a fake airline ticket conformation, or something like that. Opening this attachment will install the virus on your computer, and it will promptly go to work.
A few of the other “SPAM” style emails to watch out for:
- Fake shipping notices from UPS/FEDex/USPS and the like. You can always tell its fake if A: you didn’t order anything, B: The “logo” looks…off and C: (the best) if you hover the mouse over the link, it will have nonsense as an address. If any of these things are true, DO NOT CLICK ON THE LINK.
- Airline offers/tickets
- Things trying to sell you stuff that’s “too good to be true”
The virus is also known to exploit flaws in certain programs widely used by the internet. Stuff like Java/adobe programs and things of that nature. If you visit a “booby trapped” website, it will find these holes in unpatched software, and exploit them. The best prevention for this exploit is to make sure that you have these programs patched. Patching fixes the bugs and bad programming that lets the bad guys in.
The virus has also been known to use currently infected computers (infected with a different virus) to create holes and install the virus via piggyback.
What tools are good for stopping it?
Well, again, nothing beats common sense and a good back-up. A good back up renders their main weapon (encryption) ineffective as you already have your files backed up and ready for restore.
- Firewall: having a good external firewall (like the SonicWalls we sell) is a great weapon as it will prevent the “hand-shake” between an infected computer and the bad-guys server which severs the connection needed to encrypt the files.
- A Good Anti Virus Program: This is the last line of defense, and a well maintained (and patched!) AV software will prevent the virus from getting a hold of your computer.
We use Sophos, and they have been on top of this virus for a while, and have been working hard to be one step ahead of the bad guys. Sophos can detect “bad encryption” and shut it down before it happens.
- Prevent users from having Admin right on the computers: Even if they DO get infected, it will only lock the files in their profile, NOT the files on the network. Still not a great situation, but WORLDS better than losing a whole business’s worth of documents.
- Patch that software! Especially JAVA
- Discipline: remember no AV program or firewall in the world can stop a user from “just clicking yes” to all the prompts when ever they see them. Clicking “yes” to whatever pops up is just like giving it (the virus) permission to do whatever it wants despite all the AV software and firewalls in the world.
I hope this is informative. It is a really nasty virus that can really destroy a business if it gets a hold of the files. Ransom starts at $300, but has been known to go as high as $10,000! Even if it was paid,
There is no promise that the files will get unlocked. That few extra bucks for a sonicwall or a good backup solution will seem meager compared to having your business held hostage.
Jeffrey Blair, Technician at Mavidea Technology Group
